
More and more, our society is evolving into a culture of openness with information. This is great for economic development, education, timely exchange of information, and so many other things. But when it comes to federal contractors and one’s obligations to protect sensitive information, this culture of openness can create enormous challenges.
Those federal contractors that operate within a global organization have a particularly unique challenge as our networks and communications span the globe. The growing divide between Silicon Valley and Federal policy-makers isn’t helping the matter either, as outlined in this article from The Atlantic. Extreme takes a number of proactive measures to ensure we not only establish appropriate controls and protections for sensitive information but also adequately educate our workforce on identifying sensitive information and applying appropriate protective measures.

Many don’t understand what types of information require protection. I’m going to try and clear up some of that mud. There are essentially four basic categories of information that require protection:

Personally Identifiable Information, also known as PII, is a piece (or pieces) of information that discloses the identity of an individual. PII may contain direct identifiers (e.g., passport or driver’s license information) that can identify a person uniquely, or quasi-identifiers (e.g., race) that can be combined with other quasi-identifiers (e.g., date of birth) to successfully recognize an individual. PII can be broken down into sensitive and non-sensitive categories. Sensitive PII includes name, social security number, driver’s license number, physical address, credit card information, medical information, passport information, and financial data. Non-sensitive PII includes date of birth, place of birth, zip code, gender, race, and religion. While some PII is considered «non-sensitive», it’s important to understand that multiple pieces of non-sensitive PII may result in the disclosure of identity, thus rendering the information sensitive. It’s also important to remember that these lists are not all-inclusive, they are meant to be discussion points to help you understand the types of information that require protection.
There is quite a bit of legislation that requires adequate protection of PII, the most popular being the Privacy Act of 1974. In addition to the Privacy Act, there’s also the Fair Credit Reporting Act (FCRA), Health Insurance Portability and Accountability Act (HIPAA), Gramm-Leach-Bliley Act, and many others including contractual language that requires various levels of protection for PII. If you have active business dealings in Europe, you also must abide by GDPR compliance requirements.
If you hold a position that requires you to handle, process and/or transmits PII, it is imperative that you understand what constitutes PII and how to adequately protect this information. Some of the basics include:
PII requires protection both at rest and in transit. At rest means a file that is stored on a hard drive or server. In transit is a document or information, that is being transmitted via email, fax, mail, etc.
Negligent or ineffective handling of PII can lead to unauthorized disclosure, which can be extremely costly to the affected person(s). It’s critical for all stakeholder departments across an organization to collaborate and implement effective policies and procedures so employees are afforded the appropriate tools and knowledge to ensure adequate protection of PII.
We take these requirements serious at Extreme and have identified staff members from Federal Security, Cyber Security, HR, Legal and IT that work together to ensure our policies and procedures adequately address them.

Company proprietary is another category of information that’s important to understand, and it’s one that many companies struggle with. The FBI estimates that US companies lose over $600Billion in trade secrets EVERY year to data theft. This comes from a combination of insider threats either acting negligently or maliciously, as well as external threats accessing and stealing the data. It’s imperative for companies, and employees, to properly define and mark their sensitive information. It’s just as important to properly train employees on identifying and protecting this information.
Proprietary information is defined as information that a company wishes not to become public, and if disclosed, could cause some level of harm to the organization and/or its employees. Proprietary information commonly includes financial data, merger and acquisition plans, trade secrets, technical product data, source code, etc. This is not an all-inclusive list of what constitutes as proprietary to your organization, this is meant as an educational guide to help you understand basic concepts of protecting proprietary data.
As with PII, there is legislation that addresses unauthorized disclosure of proprietary information, the most widely known one being the Economic Espionage Act of 1996. This law focuses on the protection of intellectual property and trade secrets and makes it a federal offense to knowingly disclose such information to competitors and/or persons for the purposes of gaining a competitive advantage. In addition, companies should implement policy and employment NDAs that mandate the protection of proprietary information.
At Extreme, we stress that ALL employees have an obligation to ensure proprietary information is adequately protected. Regardless of your position, you likely have access to, or knowledge of, proprietary information. Some common mechanisms of protection include:
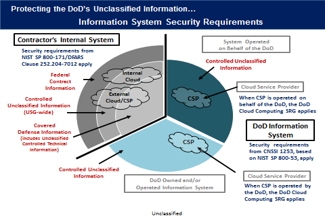
The next two categories focus on information that is owned by the Federal government. This is where you start to get into serious consequences, for both individuals and organizations, for unauthorized disclosure.
Controlled Unclassified Information, otherwise known as CUI, replaces For Official Use Only (FOUO), Sensitive but Unclassified (SBU), and Law Enforcement Sensitive (LES) categories. CUI requires safeguarding and dissemination controls pursuant to applicable laws and regulations set forth by the Federal government and the agencies for which we provide products and services. There are 20 categories of CUI as set forth by the National Archives and Records Administration (NARA). Some of the applicable categories for technology companies include:
While Federal agencies are legally obligated to properly mark and disseminate CUI, that does NOT always happen. In fact, in my experience, I’d say it rarely happens. There are dramatic inconsistencies across the government, and we continue to have a culture that simply doesn’t seem to believe protecting CUI is critical.
In a recent conversation I had with Mike Dorsey, Managing Director for Government & Public Service Security at Deloitte and retired Senior Executive at NCIS, he stated, “The government and contractors have done a great job protecting classified information, but with the expansion of CUI materials across the government agencies, there are not consistent policies and guidance for contractors to follow, putting the risk calculation and responsibilities back on corporations. So, I think this is the area that both government and corporations will need to focus their efforts, develop clear, consistent policies and procedures to protect this type of information in both the digital and physical environments.” This statement epitomizes the challenge we have with the lack of consistent policies and enforcement across the government. It places the onus on us as contractors to identify CUI and apply appropriate protections.
Despite these inconsistencies, I do believe we are headed in the right direction. Previously released FAR and DFAR clauses require defense contractors to self-certify our ability to comply with NIST800 requirements for protecting CUI. NIST800 describes the necessary information systems controls for contractors to store, process and transmit CUI on their systems. This forced defense contractors to begin assessing their cybersecurity controls and policies and improve their overall security posture. The issue with this is that it is a “self-certify” model, which allows contractors to simply check a box indicating compliance. Beginning in 2020, we will be required to conform with the Cybersecurity Maturity Model Certification, which will require a 3rd party certification of systems and processes. So instead of the current model of “check here” if compliant, contractors will be required to have an external entity come in and thoroughly assess their company’s security capabilities. This should offer additional assurance that contractors are indeed applying the appropriate security measures.
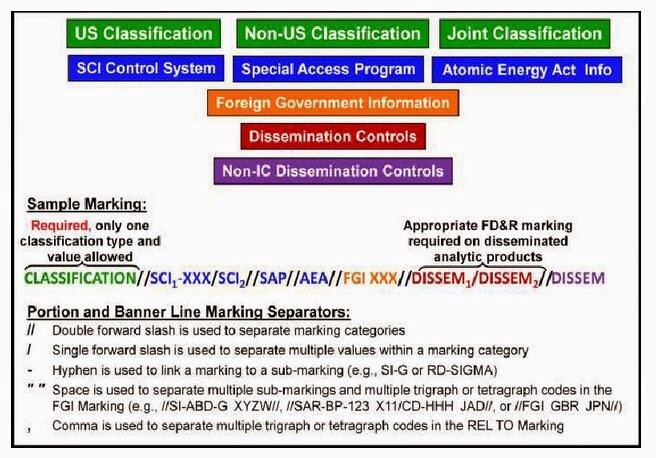
The United States has several Executive Orders and laws that govern the protection of classified information. Issued by President Obama in 2009, Executive Order 13526 replaced earlier executive orders on the topic and modified the regulations codified to 32 C.F.R. 2001. It lays out the system of classification, declassification, and handling of national security information generated by the U.S. government and its employees and contractors, as well as information received from other governments. To complement the Executive Order, some of the laws that govern the protection of classified information include the Espionage Act of 1917, the Atomic Energy Act of 1954 and the Intelligence Identities Protection Act of 1982.
Classified information typically falls into three categories that include Confidential, Secret and Top Secret. You also have information classified by the Department of Energy as Q and L, and you have SCI and SAP systems that focus on compartmentalization of sensitive intelligence and defense information respectively. Classified information is essentially information that the government has determined would cause extensive harm to national security if disclosed to unauthorized persons.
I’m going to avoid going any further into classified information as this blog is intended to focus on information sharing across an organization, and that simply should not include classified information as it is restricted to very specific environments. I’ll leave it at this, if you see classified anywhere on your corporate network or hear folks discussing classified information in unauthorized locations, notify your Federal Security team immediately.
We’ve discussed the different types of sensitive information and the importance of protecting it, but how does that work within a society that is demanding more and more openness and access? Most of us work in scattered environments that require remote access and web-based data sharing. So how does that work when your business partners in Virginia and California need to share sensitive data? How does that work when half of your IT team isn’t US-based? When you couple these internal challenges with the push from our partners and customers for near-immediate response times, it makes it extremely challenging to ensure adequate protection of sensitive information. So where is the balance? The balance lays with priorities and our priority should always rest with our legal obligations. All of us are legally obligated to adequately protect the information outlined in this blog. We are typically not legally obligated to timely response times.
We take extensive measures at Extreme to ensure these steps are incorporated into the daily routines of our team members. We do so in order to protect our team, our company, our partners, our customers, and our country’s national security.
There are several measures we can take to ensure we adequately protect the sensitive information previously discussed. At Extreme, we have four basic categories in which we apply protections that include Physical Security, Personnel Security, Information Security, and Operational Security. Let’s discuss the basics of each and how they are applied at home, in the office, or on the road.
Physical security measures tend to be the things you can see around you that are used to control access or protect sensitive assets. They include doors, locks, barriers, fences, gates, cameras, badge readers and other such measures. At Extreme, we deploy a combination of these mechanisms in our offices to help control access to our space. All exterior doors remain locked and require an active employee badge to enter. We require all visitors to access the main entrance, sign in, and be escorted by an Extreme employee. We also have cameras that are strategically placed near our more sensitive locations, such as labs, server rooms, engineering suites, and so forth. We don’t ask our team to buy a safe or CCTV systems for their homes, but there are basic measures we require to physically protect sensitive information in home offices. First, there should be a designated area where you conduct work in your home. This space should remain clean and organized so you are easily able to identify media or documents that contain sensitive information. You should also have the ability to store papers, storage devices, laptops and other forms of media that contain sensitive information in a locked location. This can be achieved with a locking cabinet of some type that has either a key, combo or biometric lock that limits access.
Where we become the most vulnerable is while we are traveling. Between the airport, the Uber or taxi, the customer’s or partner’s office, or the hotel, these locations offer the highest risk for lost or stolen items. Whenever you travel, take the minimum number of documents and physical media necessary for the trip. Always keep sensitive items in your possession or locked away in a secure location [NOTE: leaving documents sitting on top of the desk in your hotel room is NOT a secure location]. Wherever you may be conducting business, be aware of your surroundings and always take that extra step to ensure you apply adequate protections to information.
We recently enhanced our data protection policy at Extreme to include specific requirements for team members on travel.
I understand that many of us have limited budgets to work within the security industry. Not all of us are afforded the opportunity for 24/7 guard service, state-of-the-art CCTV systems, biometric access readers and so forth. But there are simple measures you can put in place that will enhance the security posture at your organization. The big thing is for your entire staff to understand that security is a shared responsibility! It’s up to the entire organization to understand the policies and procedures and to report deficiencies or non-compliance.
Personnel security (PERSEC) refers to steps taken to adequately screen the people granted access to sensitive information. PERSEC measures ensure only those individuals with a need-to-know are provided access.
We use several PERSEC measures at Extreme, both on the commercial side and the federal side of the business. Prior to each employee’s first day, they are required to complete a comprehensive background check.This background check screens for criminal history, employment records and other areas applicable for employment. On the federal side, we require any employee requesting access to our federal business data or federal facility to be sponsored by an Extreme Federal manager and provide adequate justification for access. These employees must complete comprehensive training prior to being granted access as well as annually thereafter. All employees sign an NDA upon employment agreeing not to disclose sensitive information to unauthorized persons, and we also have our partners, contractors and consultants sign similar NDAs.
For those with security clearances, this becomes even more complex. Their background check includes the completion of a 136-page personal questionnaire that covers their entire life and includes a background investigation that takes 12-18 months. In many cases, cleared employees must submit to a new investigation every 5 years and many are required to take a polygraph every 5 years. Your part in PERSEC is to ensure anyone you intend to share information with has been approved for access and has a need-to-know the information. We also have a robust security training & awareness program that includes onboarding training, annual refresher training, quarterly newsletters, webinars, blogs and other resources that ensure our team members are fully aware of our policies and procedures, as well as current events and threats, and any changes that may be occurring relevant to security.
Information security (INFOSEC) applies to the measures taken on systems and networks to protect information. We have a dedicated group of INFOSEC specialists at Extreme that work tirelessly to protect our network. Our cybersecurity team, led by Phil Swain, drafts and implements policy, recommends security controls to the IT team, conducts investigations, and reports regularly to the executive team on findings and recommendations. Our cybersecurity team has been heavily involved with setting up extra security measures for our federal business. We have taken steps to ensure appropriate compartmentalization of information with dissemination restrictions, we have a reporting process for any cyber incidents involving federal staff members and/or federal data, and our Federal Security Director is a member of the INFOSEC Steering Committee, which meets monthly to discuss INFOSEC-related matters and establish INFOSEC policy. Some INFOSEC measures we take at Extreme include:
Your role in INFOSEC is understanding the policies, adhering to them, and reporting any suspected violations. Be sure you understand the policies and the tools that are available, and when in doubt, ask for guidance!
Operational security (OPSEC) refers to how we apply security in our day-to-day activities. OPSEC is arguably the most important of the four security categories mentioned here. Without good OPSEC, these other categories lose their effectiveness. OPSEC is the responsibility of each and every employee at Extreme and other defense contractors…our level of success in preventing unauthorized disclosure is ultimately up to us.
Applying good OPSEC measures in your day-to-day activities is not as cumbersome as it may seem. Some examples of good OPSEC include:
This is obviously not an all-inclusive list of OPSEC measures that one can take during the course of a day. This is meant to be a stimulant…it’s meant to get you to think about how you can help yourself be more secure at your organization. These little steps really do matter. They could be the difference between a quiet Friday night or your organization being the headline on the evening news.
An aggressive reporting program is a great tool in combating unauthorized disclosure of sensitive information, but it is only effective if the program is properly used. A successful reporting program relies on a team having the knowledge and understanding of reporting procedures while having the willingness to report without fear of retaliation.
We take this matter very seriously at Extreme and offer a number of ways in which team members can report suspected disclosure or violations. We offer an online reporting tool that has an option for anonymity, a reporting hotline, and our security staff is readily accessible both online and in our federal office. It’s critical for team members to have multiple options for reporting given how to spread out we are geographical. These options allow for more timely reporting and response. But it’s just as critical that team members are comfortable reporting suspected disclosure or violations without the fear of retaliation. This comes with establishing security support and culture from the top of the organization.
In closing, we are ultimately responsible as individuals and organizations to protect sensitive information. This information includes personal information, proprietary, customer and partner data, and federal data. Each of these various types of information has Executive Orders and laws that govern its protection. It’s imperative to understand these laws and apply the appropriate protections during your day-to-day activities. It’s just as important to find ways to run your business with speed and efficiency while applying these protections. That is the delicate balance we try to achieve here at Extreme with our policies and procedures. The best way to build a successful security program that will meet these requirements is to have senior leaders, across the key functional pillars of your organization, be stakeholders and active participants in the design, rollout, education, and enforcement of your data protection policies. At Extreme, we incorporate Federal Security, HR, Legal, IT, Cyber Security, Sales, Engineering and other departments into the design and approval of our policies. This collaboration ensures we balance controls and restrictions with appropriate process efficiencies that allow our business partners to operate at optimal levels.