
What’s This Demo All About?
Extreme Networks will be presenting a laser tag demo in booth #519 at the Supercomputing Conference 2017. This interactive demo will show an event-driven example of our automation and orchestration suite, Extreme Workflow Composer, integrating with a legacy system for enhanced control over network behavior.
In this demonstration, our laser tag target is connected to an Internet of Things (IoT) sensor. When the target, a Purple People Eater, is hit an automation workflow is triggered. The workflow reconfigures a switch to allow IP multicast video to flow from a source to a receiver for 60 seconds. When the 60 second timer expires, the switch is again reconfigured and the video stops waiting for the user to hit the target and trigger the workflow again.
Stop by SC17 booth #519, to see our demo in action and have some fun yourself!
Want more details? Learn how the demo is going to operate with Extreme Workflow Composer below.
Introducing Extreme Workflow Composer
The Extreme Workflow Composer is a platform for integration and automation that is based upon the opensource ‘Stackstorm’. Stackstorm provides the event driven framework and includes common components, called ‘packs’ that extend the Extreme Workflow Composer’s capabilities to interface with external systems. A workflow can be triggered by a rule in several ways: manually, periodically, or driven by external events as is the case with the laser tag demo. A sensor is software or scripts used to inject external events to workflow composer where they are evaluated against rules. If the data sent from the sensor passes the criteria defined in the rule then the appropriate workflow is triggered. Workflows define the actions that are going to be executed and in what order. Workflows can be nested and composed of other workflows. Actions can be anything that is ‘executable’ on an operating system, local or remote.
What’s Possible the Extreme Workflow Composer?
Shown in the blue boxes below, a pack is a bundle of sensors, rules, workflows and actions built to serve a specific purpose. These packs are available on the Stackstorm Exchange. Although not inclusive of all the available packs, the graphic gives us a quick understanding of what’s possible.

Utilizing Data Center Fabrics
In addition to the open source packs, Extreme supports a pack called Data Center Fabric that simplifies the complexities of deploying fabrics across multiple devices. The administrator only needs to complete a short form, point, and click to deploy and maintain a Data Center Fabric. Workflows decrease the opportunity for human error, reduce the time to deploy, and ensure consistency. The configuration happens without error in minutes instead of hours.
Extreme Workflow Composer provides a simple to use graphical way to define workflows called Workflow Designer. You just drag an action from one of the packs on the canvas and click to connect that block.
Constructing and maintaining a workflow with Workflow Designer is quick and easy because it self-documents. This is important, especially when you need to make changes to your processes as your business needs change.

Understanding the Workflow Designer Graphical Interface
In addition to the automation and orchestration, Extreme Workflow Composer keeps a history of every workflow that was run and the results of each action. Easy to see at a glance, a green circle indicates the action completed successfully, while a red circle indicates that the action failed.
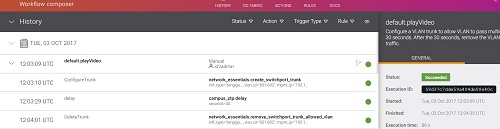
Viewing the Workflow Composer History
Administrators can drill down to look at the result of each action recorded in the history to determine root cause of failure. This is a great utility for forensics and trouble shooting.
Staying Cyber Secure
Attackers are becoming more and more sophisticated each year, armed with new techniques and tools. Workflows can be constructed to coordinate responses to cyber security threats. Consider the case where a threat is detected, Extreme Workflow Composer matches this threat to a rule that specifies the workflow must lock down the service (because it’s under attack), channel the traffic to a honey pot, and record the intruders attempt to exploit the network. This use case could have implications for configuring routers, switches, firewalls from multiple vendors, as well as spinning up new virtual machines. All of this can be orchestrated and automated with Extreme Workflow Composer as events happen.
For more information on the upcoming SC17 Laser Tag Demo, visit Extreme at booth #519.
To learn more about the Extreme Workflow Processor, please visit our product page.